Introduction to VLAN
VLAN, the English full name of Virtual Local Area Network, is a kind of network technology, which divides the equipment into different network segments logically to realize the virtual working group technology. It is not limited by the physical location. VLAN allows computers and users in the network to communicate in the simulation environment, just like they exist in a single LAN, and share a single broadcast and multicast domain.
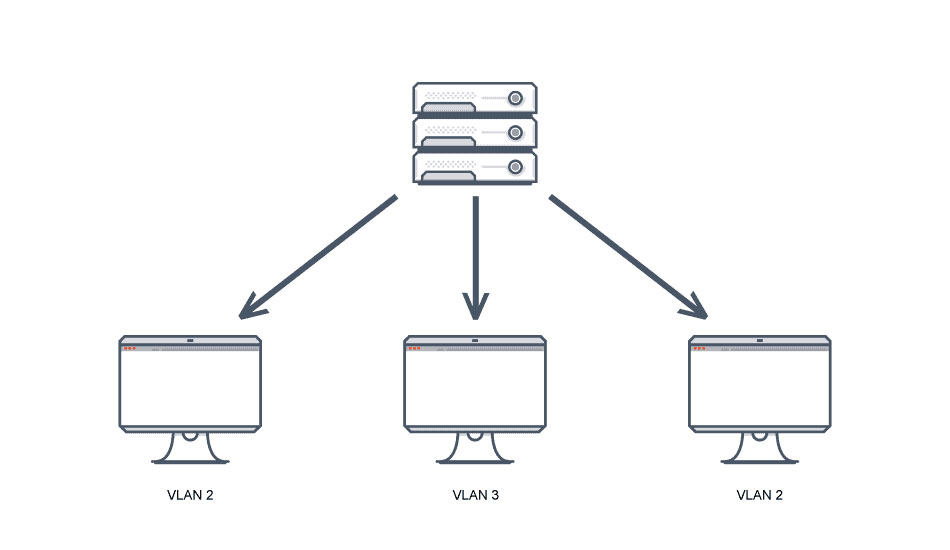
The implementation of VLAN is mainly to solve the broadcasting problem and security of Ethernet. The broadcasting and unicast traffic in one VLAN will not be forwarded to other VLANs. Even two computers in the same network segment, if they are not in the same VLAN, their respective broadcast streams will not be forwarded to each other.
At the same time, VLAN can achieve scalability, security and easy network management, which can help quickly adapt to changes in network requirements and network node re-deployment.
VLAN protocol
VLAN protocol will add VLAN label in data package, and VLAN label of Ethernet network shall comply with IEEE 802.1Q industry standard. The 802.1Q label consists of 32 bits (4 bytes) of data inserted into the header of an Ethernet frame. The first 16 bits of this field contain the hard-coded number 0x8100 so that the Ethernet device recognizes that the frame belongs to 802.1Q VLAN. The last 12 digits of this field contain VLAN ID numbers from 1 to 4094.
The 802.1Q label fields are as follows
Label protocol (2 bytes): fixed value 0x8100, representing 802.1Q label.
User priority (3 bits): represent service level QoS
Specification format indicator (1 bit): for compatibility between Ethernet and token ring.
VLAN ID (12 bits): VLAN ID number, used to distinguish VLANs on the link.
VLAN classification

Static VLAN
Based on port
VLAN determination according to the port division of the switch
Dynamic VLAN
Based on MAC address
VLAN division according to MAC of connected equipment
Based on Subnet
VLAN division according to IP network segment of connected equipment
Based on user
Divide VLANs according to the login user of the computer
When VLAN is required
As shown in the figure below, PC1 under switch SW1 needs to communicate with PC3 in two two-layer switch networks. The data frame must specify a destination MAC address for communication, so PC1 must first broadcast an “ARP Request” message to attempt to obtain the MAC address of PC3. ARP request will be forwarded to PC in all network under router, including all equipment under SW2. This could create a network storm, causing network congestion and security issues.
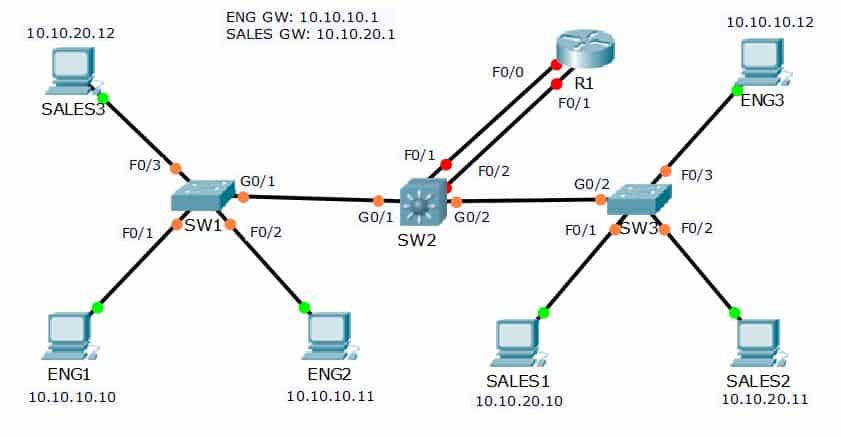
In this case, VLAN is an economical and secure solution.
The following is a simple example of creating a VLAN on an industrial router.
Through the division of VLAN, the network port (SW1 access) pointed by the green line is divided into VLAN1, and the network port (SW2 access) pointed by the blue line is divided into VLAN2. In this way, when PC1 needs to communicate with PC3, the message will only be broadcast to the equipment under SW1, but not to the equipment under SW2.
Benefits of using VLAN
Improve safety
In a VLAN network environment with multiple broadcast domains, the network administrator can control each port and user. Malware users cannot sniff network traffic at will by accessing any switch port. The network administrator controls each port and the resources it allows to use.
Higher performance
Dividing the network into different virtual subnetworks can reduce unnecessary traffic, reduce delay and traffic load of the network and network equipment, and improve performance.
Cost reduction
By dividing a smaller VLAN on a switch, multiple network segment division and isolation are realized without adding additional routers, and equipment investment is reduced.
Simplified network management
VLANs can also be divided across regions and ports, so that administrators can configure and manage devices under the same VLAN in a centralized environment.